Bitcoin Plan - March 24, 2021
How much bitcoin is enough?, SIM Swapping Attacks, and Tesla News
Dear Bitcoiner:
I often get asked, “how much bitcoin should I have before I worry about an estate plan.” It’s a difficult question to answer for a couple of reasons…
Every bitcoin plan involves planning, protecting and preserving your deflationary hard money that is expected to continue maintain its value and rocket when compared to “dirty government drug money” (pronounced “fiat”);
Only a portion of effective Bitcoin Planning focuses on how much you hodl; and
Bitcoin focused planning lawyers have a duty to educate Bitcoiners about the importance of proper planning and the cost of no planning or poor planning
Anyone that plans to hodl their bitcoin long term, regardless of how much you hodl, should be concerned about implementing a bitcoin estate plan. If this is not something you have considered, you are not alone. Most Americans overlook or do not understand why planning for the future is so important. So, let me give you some statistics that are worth considering — bear in mind that the following information relates to Americans, not just Bitcoiners looking to plan:
49%: Percentage of Americans who do not believe their assets are worth enough to worry about estate planning.
47%: Percentage of Americans who believe estate planning is mostly for the ultra-wealthy.
72%: Percentage of Americans who do not have a will that accurate reflects the value of their assets.
15%: Percentage of Americans earning more than $150,000 who have an up-to-date will.
6 months to 2 years: The amount of time an average modest estate can take to get through the probate process.
35%: Percentage of Americans who have either personally experienced or know someone who has experienced family conflict as the result of not having an estate plan or comprehensive will.
74%: Percentage of Americans who said they would be more likely to create an estate plan if it helped lower their families' taxes.
I think it is worth mentioning that an effective bitcoin plan, will help you and your family:
Protect and preserve the value of your bitcoin for generations to come.
Help obfuscate your identity on exchanges and fiat on/off ramps.
Lower your families tax obligation during your lifetime.
Lower your families tax obligation at your death.
Avoid probate administration and related expenses.
And much more!
It is never too late to get started planning for you and your family’s future. Should you wish to schedule a time to chat about your plans, feel free to use this link: Bitcoin Estate Planning Consultation.
SIM Swapping on the Rise.
If you still use your phone number for identity verification to access your bitcoin, consider this a warning. Not only is SMS for two factor authentication (2FA) an incredibly weak means of protecting your bitcoin but SIM Swap attacks, according to Federal Trade Commission, are on the rise again. If you aren’t sure what Sim Swap Attacks are you can find an overview of SIM Swap Scam here.
The most likely reason that SIM swapping attacks are on the rise is due to the low-cost associated with executing the attack as well as the low barrier of entry for non-technical scammers. The practical reality is that if you secure your bitcoin with SMS 2FA, you are vulnerable to this attack.
In a 2020 study of Wireless Carrier Authentication for Sim Swaps, research discovered how simple SIM swap can be, especially if some level of information has been leaked.
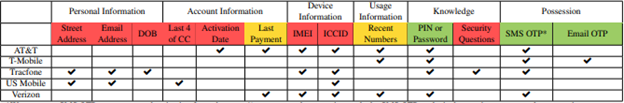
This chart denotes the authentication methods that a 2020 study on this issue observed for each carrier. A checkmark means that a type of information was a component of at least one pathway for SIM swap customer authentication.
It is worth noting that the following information was used to successful SIM swap customer phones during this study:
Recent numbers. We also found that using information about recent calls for authentication is exploitable. Typically, Customer Service Representatives (CSR) requested information about outgoing calls. Consider the hypothetical following attack scenario: Using only the victim’s name and phone number, our simulated adversary could call the victim and leave a missed call or message that would prompt the victim into returning the call to a number known to the attacker. This call would then appear on the outgoing call log and the attacker could use it for authentication. CSRs appeared to also have the discretion to allow incoming call information as evidence for authentication at AT&T, T-Mobile, and Verizon. An attacker can trivially generate incoming call records by calling the victim.
Personal information. The study found that Tracfone and US Mobile allowed personal information to be used for authentication.
Account information. We found that AT&T, US Mobile, and Verizon allowed authentication using account information. As with personal information, this information would often be readily available to an adversary.
Device information. We found that all carriers except for T-Mobile use device information for authentication. These authentication methods included the customer’s IMEI (device serial number) and ICCID (SIM serial number). Both the IMEI and ICCID are available to malicious Android apps, and IMEIs are also available to adversaries with radio equipment.
Security questions. We found that Tracfone used security questions for authentication. We also found that T-Mobile, Tracfone, and Verizon prompted users to set security questions upon signup. Prior research has demonstrated that security questions are an insecure means of authentication because answers that are memorable are also frequently guessable by an attacker.
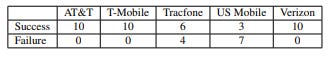
The outcome of the study documents that all attempts for SIM Swap Requests were successful at major carriers.
Better Authentication is Required.
In summary, the best piece of advice I have discovered to date comes from Jameson Lopp,
“Do secure your private keys with hardware devices and multisig. Don’t use browser-based wallets as they have huge attack surfaces. Do use hardware-based 2FA for any web app that supports it. Don’t use SMS 2FA or enable online accounts to be reset/recovered via a phone number.”
TL;DR SMS as Two Factor Authentication is very weak. Consider hodling with a hardware device and multisig.
Bitcoin News and Announcements
Free Sats for Reading
Below is a QR Code, Bitcoin lightning faucet. Using your favorite lightning wallet, simply scan the QR Code and receive your Sats. Sats are limited. First come, first serve.
Hope you found value in this week’s issue. If you have any friends that are looking to find out more about Bitcoin or Bitcoin Planning have them sign up for this newsletter here:
Thanks for reading! @BitcoinPlanner